Email is one of the biggest cyber security challenges facing not just estate agents but all businesses today. Research conducted by Microsoft indicates that over 90% of cybercrime begins with email, so it’s important that every organisation has a plan to prevent these threats reaching staff.
The reason email is the prefered choice of cyber criminals is simple – it bypasses the technical measures and protections your IT administrators have put in place and preys on the social fallibility of people working within the organisation to unknowingly breach your cyber security.
A sophisticated or targeted breach can be devastating, with criminals then able to embed themselves within your IT estate, sometimes installing backdoors making themselves perrenial, which can then require a complete rebuild of networks, devices, and infrastructure to ensure bad actors don’t still have access to your data. Late last year, the conveyancing firm Simplify was victim to a cyber security incident which directly obstructed business for weeks and ultimately took months to fully remedy. I observe now that solicitors have created landing pages allowing canned legal claims against Simplify for the disruption caused to property transactions, which I’m sure is one of many knock on effects from this incident which has distracted Simplify from its core business for much of this year.
This is why paying attention to your cyber security practices proactively is so important: because if you are unfortunate enough to suffer a breach, despite you being a victim of crime, the attention of your customers and the media will not be of pity, but rather of skeptism regarding your processes put in place to prevent the breach (e.g. security), and measures applied to minimize the damage should there be one (e.g. encryption). Don’t be one of the businesses closing the stable door after the horse has bolted, much like Uber, seen hiring for an increased number of cyber security professionals following their breach this month.
So how are the criminals breaking in?
1) Spear phishing
Spear phishing is a targeted, often researched cyber attack. The research allows the criminal to appear legitimate to your member of staff. This is a particular threat to agencies who tend to communicate personally identifiable information about their customers, or the nature of their business via email. Bear in mind, if a hacker has gained access your clients email, they may know a huge amount of information about names, places, dates and amounts that would lead you to believe the communication is genuine.
2) Business Email Compromise
“Hi John it’s Mary here at accounts. The supplier at Queen Street have issued this invoice and it’s urgent we pay this today…”
Business email compromise is an advanced form of spear phishing where the criminals will impersonate key members of your staff, either to other staff in your organisation or to your clients. This attack is most commonly seen in the property industry as fraudsters sending false bank details during the conveyancing process to persons about to commit to a transaction, such as a deposit.
3) Ransomware, trojans, malware
“There is a tax issue on your account. Click this link or face legal consequences”
Usually the first phase in an attack, the criminal will attempt to trick a member of your staff into opening an attachment or link which causes their computer to run a malicious program of software (malware). Because the program is running within your IT estate, it is often the case that such programs can run rampant stealing, damaging or holding to ransom your business data across all departments. Many businesses are surprised that their backup and disaster recovery plans fail entirely when faced with ransomware – which can end up unfortunately ransoming the backups and cloud-stored data as well if they are not properly protected. Fortunately, your IT administrator can help protect against this by running and maintaining anti-virus software, but do make sure this is running on all devices (difficult when staff are using their own phones!).
How can we improve?
Don’t rely on email for communicating sensitive business transactions. Use it to arrange people into safe spaces to conduct business, such as face to face meetings or secure property technology platforms where the identity of your customer is verifiable.
Most agents I have worked with have been using Microsoft Outlook as their app for working with email. By integrating property technology into Outlook directly, we can help make email more secure.
- Clients will always end up using email to communicate with your business, even when other solutions exist, such as a portal app. They will take the path of least resistance to them and follow the process they are the most familiar with. Access to email is ubiqitious, access to your app might not be.
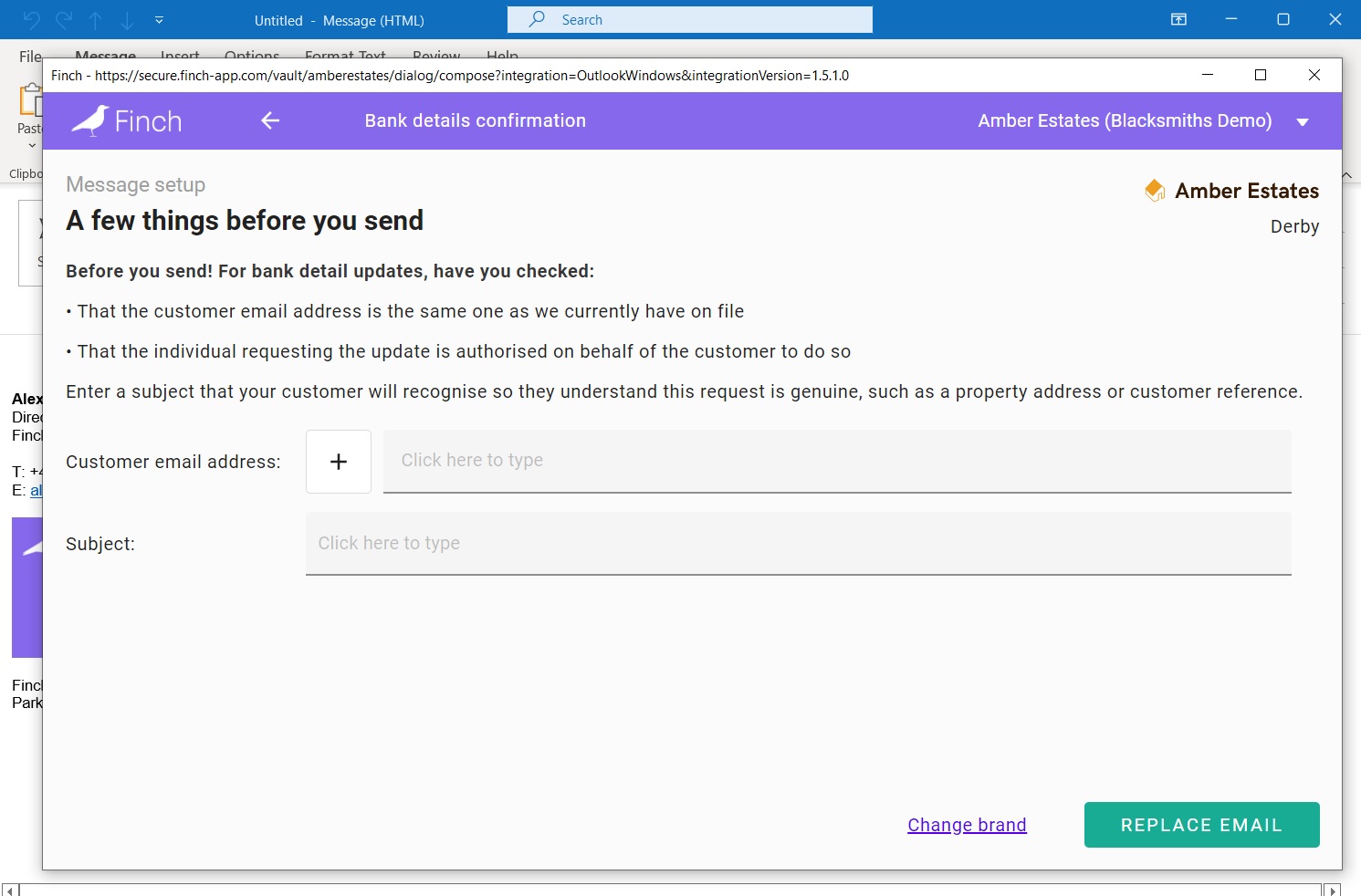
- Thus, your staff will receive requests for account changes or personally identifiable information via email. It’s easiest if your staff can respond intuitively from within Outlook to close the opportunity for a potential threat to be realised.
- For instance, when receiving a request to change bank details, your staff can now be prompted with your (customizable) notices to them helping them further secure that request, like so:
If you’d like to learn more about how Finch can protect your organisation from email threats, please get in touch, or join our newsletter for more tips.












